Introduction
AWS Command Line Interface (CLI) is a unified tool that allows you to manage your AWS services from the comand line. This guide will take you step-by-step through the installation and configuration of AWS CLI.
Prerequisites
- An active AWS account
- AWS credentials (Access Key ID and Secret Access Key)
- A Linux operating system
- Administrative rights on your machine
- Checking the existing installation
Before proceeding with a new installation, check whether AWS CLI is already installed
aws --version
2. Installing AWS CLI
On Linux (Debian/Ubuntu)
sudo apt-get update
sudo apt-get install unzip curl
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws-cli-install
3. Initial configuration
Configuring AWS CLI requires four main pieces of information
aws configure
You will be asked to enter :
- AWS Access Key ID
- AWS Secret Access Key
- Default region name (e.g. eu-west-3 for Paris)
- Default output format (recommended : json)
Structure of the configuration file :
~/.aws/credentials : Stores your credentials
~/.aws/config : Stores the general configuration
# ~/.aws/credentials
[default]
aws_access_key_id = YOUR_ACCESS_KEY
aws_secret_access_key = YOUR_SECRET_KEY
# ~/.aws/config
[default]
region = eu-west-3
output = json
4. Checking the configuration
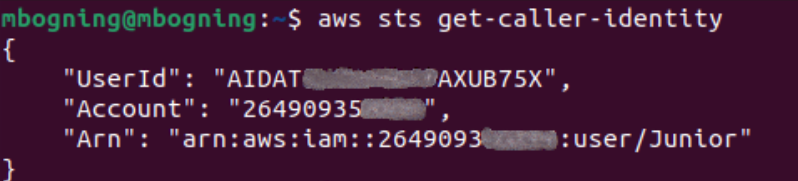
To check that your configuration is correct :
aws sts get-caller-identity
The command should return your AWS identity information :
5. Good safety practice
- Regular key rotation: Change your access keys regularly
- Minimum permissions: Use the principle of least privilege
- Multifactor Authentication (MFA): Enable two-factor authentication
- Multiple profiles: Use different profiles for different accounts
Configuring multiple profiles
aws configure --profile prod
aws configure --profile dev
Use of a specific profile :
aws s3 ls --profile prod
Conclusion
AWS CLI is a powerful tool for managing your AWS resources. Correct configuration is essential for secure and efficient use. Don’t forget to keep your credentials up to date and to follow good security practices.

